
Hybrid work, hybrid clouds, and distributed enterprise architectures have made one thing clear: security can no longer be built around a single perimeter. Today’s networks span branches, multi-cloud workloads, data centers, and thousands of IoT and remote endpoints. Yet many organizations still operate siloed firewall architectures that weren’t designed for this reality — leaving them with fragmented visibility and inconsistent policy control.
According to Gartner’s Magic Quadrant for Hybrid Mesh Firewalls (August 2025), enterprises are rapidly shifting from isolated perimeter firewalls to hybrid mesh firewall architectures that unify policy, visibility, and threat prevention across physical, virtual, and cloud deployments.
Main factors driving this shift include:
Traditional firewalls, struggle significantly in this context. For example:
A Hybrid Mesh Firewall solves the weaknesses mentioned above. According to Gartner, a Hybrid Mesh Firewall (HMF) is a unified security architecture that replaces siloed, perimeter-based firewalls with a distributed enforcement model spanning data centers, branch sites, multicloud environments, micro-segmented networks, and remote users. It delivers a consistent security policy, centralized orchestration, and shared threat intelligence across heterogeneous environments using a cloud-based management plane. Unlike traditional NGFWs tied to static locations, HMFs support secure connectivity via IPsec, SSL VPN, and ZTNA while incorporating advanced threat detection, including DNS security, IoT/CPS device discovery, behavioral analytics, and risk scoring. A true HMF enables orchestration and automation at scale with zero-touch deployment, multicloud policy synchronization, AI-assisted troubleshooting, and APIs for integration and security-as-code automation. It consolidates visibility and control across hybrid deployments, integrates with IT and security ecosystems such as ITSM, SIEM, identity, and SASE/SSE, and leverages AI-driven threat correlation and prevention for faster, more adaptive protection.
Versa NGFW fully aligns with Gartner’s Hybrid Mesh Firewall model by delivering centralized policy, distributed enforcement, and unified visibility across hybrid and multicloud environments. Versa provides a single-policy framework across branches, data centers, and multiple clouds, with AI-powered analytics for event correlation and anomaly detection. It delivers advanced threat prevention with IPS, SSL inspection, DLP, and DNS security while maintaining high performance. Available as hardware, virtual, or FWaaS, Versa applies consistent enforcement from edge to cloud and integrates with ITSM, SIEM, SOAR, and identity platforms through open APIs. With zero-trust segmentation and AI-driven threat correlation, Versa meets all the core requirements of a true Hybrid Mesh Firewall.
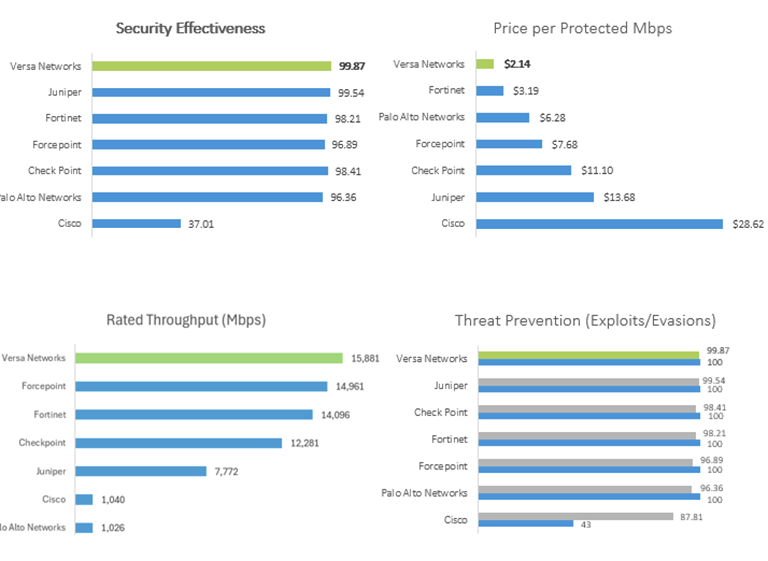
Figure: Versa outperforms all Tier-1 enterprise firewalls in security effectiveness, performance, threat prevention, and total cost of ownership – Source: Cyberratings
For network security leaders, the real differentiator is not just whether a firewall stops threats — but whether it can do so everywhere the network lives, without multiplying complexity or cost. Versa NGFW delivers:
These outcomes align with Gartner’s central tenets of a hybrid mesh firewall: centralized visibility, orchestration, automation, and consistent cross-environment enforcement
As hybrid networks expand, customers expect their NGFW to deliver the visibility, consistency, and intelligence needed to secure every edge — physical or virtual. With unmatched performance, proven threat prevention, and the lowest total cost of ownership among Tier-1 firewalls, Versa sets the benchmark for next-generation protection in a hybrid mesh firewall world.
Subscribe to the Versa Blog