
For enterprises everywhere, understanding and defending against sophisticated cyberattacks is crucial in today’s threat landscape of ubiquitous attacks. The MITRE ATT&CK framework, developed by the non-profit organization The MITRE Corporation, is a comprehensive knowledge base that details adversary behavior across the full spectrum of attack stages, from reconnaissance to impact. Originally created for the U.S. Military, it has become a global standard for security professionals, providing in-depth descriptions of the techniques attackers use, as well as effective detection and mitigation strategies. By offering a structured approach and categorizing attacker behavior into a comprehensive matrix of tactics, techniques, and procedures (TTPs), organizations can use the MITRE ATT&CK framework to enhance their cybersecurity posture.
One important use of the ATT&CK framework is in threat detection and response. By mapping detected threats to the ATT&CK framework, security teams can identify gaps and improve incident response processes. This is also where Versa’s Advanced Threat Protection (ATP) can provide a multiplier effect for an organization’s cybersecurity strategy.
Versa Advanced Threat Protection (ATP) is a comprehensive cybersecurity solution designed to protect organizations from sophisticated threats across various vectors. It integrates seamlessly with the Versa ONE Unified SASE platform, offering a multi-layered defense that leverages advanced techniques such as: static analysis to examine file attributes, dynamic analysis sandboxing, AI/ML-based behavioral analysis, and multi-AV engine detection. By analyzing traffic across multiple file types, Versa ATP can detect and mitigate both known and unknown threats in real-time. Through these techniques, Versa ATP can catch zero-day exploits and other advanced attacks that traditional security measures might miss.
Knowing how many of our customers use the framework, Versa has purposefully aligned the detection and reporting capabilities of ATP with the MITRE ATT&CK framework. This alignment is particularly practical considering we provide security controls across all stages of the attack lifecycle.
The MITRE ATT&CK framework is made up of three ATT&CK matrices: Enterprise, Mobile, and Industrial Control Systems (ICS). For this blog, we’ll focus on the Enterprise matrix.
Each ATT&CK matrix is organized into three main components: tactics, techniques, and sub-techniques.
There are fourteen tactics in the enterprise ATT&CK matrix, described briefly below.
| Tactic | Description |
| Reconnaissance | Information gathering to plan future attacks |
| Resource Development | Acquiring resources (e.g. tools, infrastructure, accounts) in preparation for an attack |
| Initial Access | Gaining unauthorized entry into a target environment |
| Execution | Running malicious code on a target system |
| Persistence | Maintaining a foothold in the system over time |
| Privilege Escalation | Gaining higher-level permissions on a system |
| Defense Evasion | Avoiding detection and bypassing security controls |
| Credential Access | Stealing account names and passwords |
| Discovery | Identifying and exploring the network, devices, and services |
| Lateral Movement | Moving through a network to access other systems |
| Collection | Gathering information from compromised systems |
| Command and Control (C2) | Communicating with compromised systems to control them |
| Exfiltration | Stealing data from the target environment |
| Impact | Disrupting, destroying, or manipulating systems or data |
The number of tactics, techniques, and sub-techniques for attack indicate the varied types of cyberattacks organizations must guard against. Here’s how Versa ATP works with other key components of Versa’s comprehensive SSE security suite to protect against tactics defined in the MITRE ATT&CK framework.
Versa ATP uses an intelligent blend of AI-driven file analytics and sandboxing to isolate and analyze suspicious files in a controlled environment. Designed to detect attacker deception techniques, Versa ATP is particularly useful in protecting against advanced persistent threats (APTs) and zero-day attacks.
Versa UEBA leverages AI/ML to detect suspicious activity by analyzing the behavior patterns of users and devices across the network.
Versa IDS/IPS protects against malicious activities across the network by analyzing traffic patterns, blocking unauthorized access, and ensuring compliance with enterprise security policies.
Versa DLP prevents the unauthorized transfer and exfiltration of sensitive data across the network. It monitors and controls data flows, ensuring compliance with data protection regulations and preventing data breaches.
Through its alignment with MITRE ATT&CK framework, Versa ATP helps organizations defend against the full spectrum of cyber threats. In fact, Versa’s detection reports automatically show each detection and its corresponding place in the ATT&CK framework.
Let’s break down Versa’s detection mapping to the MITRE ATT&CK framework with an example using Black Basta ransomware.
For background, Black Basta is a sophisticated ransomware-as-a-service group that emerged in 2022, quickly establishing itself as a significant threat to organizations across various industries. Black Basta is infamous for its double-extortion tactics – the group encrypts victims’ data and demands a ransom, threatening to leak sensitive information if the ransom isn’t paid. With global enterprise targets across a variety of business sectors, Black Basta has already claimed several hundred critical infrastructure and healthcare victims in the U.S. Black Basta typically uses phishing and vishing (voice phishing) scams to gain initial access, although they have also exploited critical vulnerabilities.
The image below shows a Versa ATP report of a detection of Black Basta.
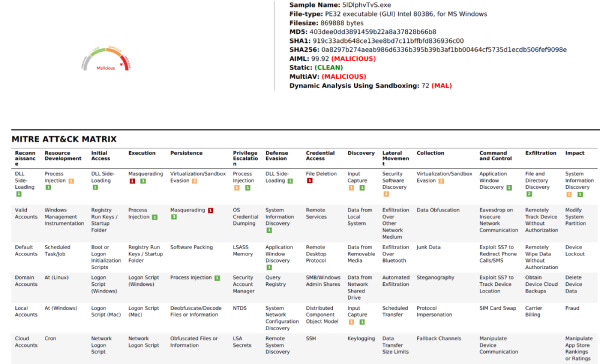
Versa’s report pre-maps detected tactics and techniques to the MITRE ATT&CK framework, so we can easily reconstruct what Black Basta would have done had Versa not caught it.
Below is a summary of what would have likely happened in the attack.
In addition to these actions, specific deleted tripwire files, commands used for communicating with the C2 servers, and specific file paths encrypted attributed this attack to Black Basta.
Versa ATP plays a key role in strengthening an organization’s cybersecurity initiative. With Versa’s detection reports, security teams get a fingerprint of the attack, which can be used for attribution to known adversaries, incident response, simulation attacks, and other security measures. Our mapping to the MITRE ATT&CK framework allows organizations to easily use Versa data to enhance other security processes using the framework. By aligning with the MITRE ATT&CK framework, Versa ATP provides a comprehensive view of the tactics and techniques used by attackers, allowing security teams to identify and address vulnerabilities across all layers of their infrastructure.
To learn more about Versa ATP and our threat defense capabilities, contact your Versa rep or schedule a demo.
Subscribe to the Versa Blog