
In an SD-WAN deployment, your edge appliances are often placed in branch offices, industrial sites, or other remote locations where you may not have constant on-site oversight. If one of these appliances is moved — whether for legitimate reasons such as RMA replacement, storage, or shipment to another site, or due to tampering, theft, or unauthorized relocation — it can disrupt connectivity, service disruption, and in some cases violate compliance requirements.
Appliances at the edge hold the keys to your network. If one is moved outside your control, attackers could exploit it to gain unauthorized access to credentials, exfiltrate sensitive data, or cause outages. Even unintentional movements — like devices being stored, shipped, or replaced — can create visibility gaps and compliance concerns.
The risks are clear:
This makes unauthorized device movement detection not just a “nice-to-have,” but an essential layer of defense.
Most SD-WAN vendors limit movement tracking to GPS coordinates or geofencing, which can show when a device crosses a boundary or shifts on a map. While useful, this leaves significant blind spots. A device that goes offline — whether for legitimate reasons like shipment, RMA, or storage, or for malicious reasons such as tampering or theft — immediately drops off the radar. GPS alone cannot verify if the appliance has been cloned, if its certificate has been tampered with, or if it is attempting to rejoin after being revoked from a customer tenancy. In other words, GPS visualization tells you where a device was, but not whether it is still trusted.
Versa addresses these gaps with a layered, telemetry-driven approach as mentioned-
Here’s how it works in practice: If you want to ensure that any appliance movement or connection change is flagged and acted on, you set up rules. These rules define the specific conditions to track and the actions the system should take when they occur. You can apply them to individual devices or to entire device groups from the controller.
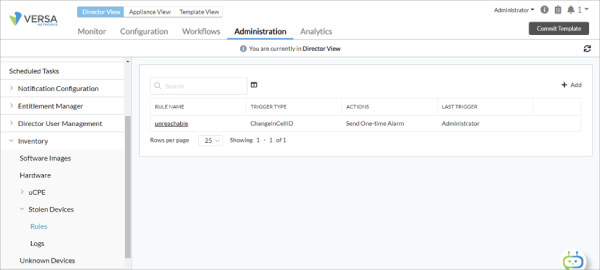
Device movement detection dashboard
From here, you can create a new rule that specifies:
By setting up these rules ahead of time, you’ve turned an unexpected incident into a fast, contained response — without scrambling or guessing.
When you need to see the full history of an appliance that’s been moved without authorization, you can pull it up in just a few clicks.
From the console, look at the inventory of Stolen Devices for Logs. Here you’ll see a record of every trigger event, when it happened, and the before-and-after details.
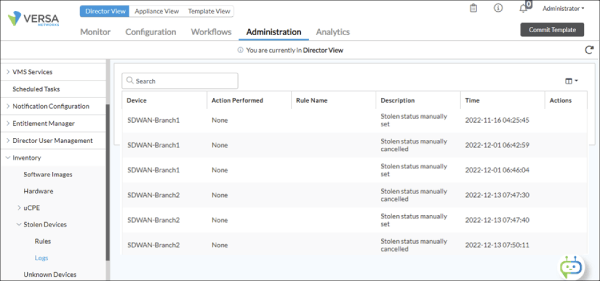
Management view showing selected devices, configurations, connectivity status, stolen suspected device indicators
This log view gives you a clear audit trail, making it easy to confirm incidents, investigate root causes, or share evidence for compliance and reporting.
If a device is marked as Stolen Suspected, you can act immediately from the unified console to secure or restore it. From the menu, go to Administration → Appliances and select the device name from the main panel. From there, you can choose to turn the device on or off, enable it to resume operation, or disable it to block network access entirely.
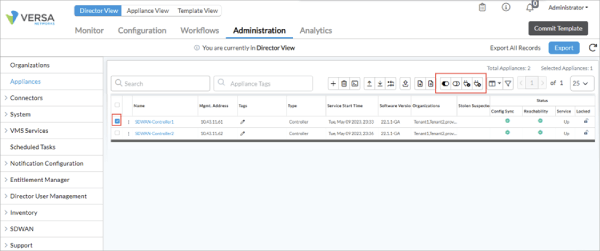
Management Dashboard with options to enable, disable, power on, or power off directly from the controller.
These controls give you the flexibility to respond based on the severity of the incident—whether that means isolating the device to prevent misuse, powering it down until it’s recovered, or re-enabling it once you’ve confirmed it’s safe.
Securing your network edge goes beyond simply knowing where your devices are located. GPS tracking alone isn’t enough — devices can be cloned, tampered with, revoked, or moved offline without detection. Versa closes these gaps with a multi-layered, telemetry-driven approach that combines real-time location intelligence, cryptographic identity binding, lifecycle visibility, and automated response mechanisms.
By continuously monitoring device signals, validating authentication through certificates, and maintaining an immutable audit trail — even for offline or decommissioned appliances — Versa ensures you retain trust, control, and compliance across your entire deployment. Versa’s Unauthorized Device Movement Detection doesn’t just track where a device is — it guarantees whether it’s still trusted, authenticated, and under your control.
You can learn more about configuring device geo-tracking and unauthorized movement detection in our documentation.
Subscribe to the Versa Blog