
Zero Trust is widely considered to be the future of security, but today it’s only used to protect remote workers. As hybrid work grows and people return to the office, many users and security teams are asking if they can use Zero Trust for their branch offices and campus sites as well.
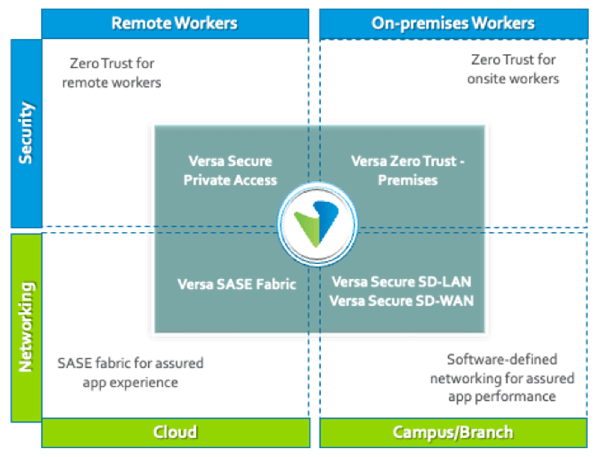
Today, with the launch of Zero Trust Everywhere, Versa delivers an integrated Zero Trust Network Access (ZTNA) solution that works for both remote and onsite users. Zero Trust Everywhere delivers a superior security model across the entire enterprise, with a single point of management and assured user experience.
Zero Trust is widely considered to be the future of security, based on the idea that no user, device, or application should be trusted by default. Security and networking leaders are embracing this security strategy in greater and greater numbers – according to a recent report by Okta 97% of organizations they surveyed are either implementing or planning to adopt the approach, and over 50% have already implemented Zero Trust. This high level of interest in Zero Trust is driven by a growing set of security challenges that legacy “perimeter” oriented security approaches struggle to address, including the adoption of cloud computing, remote work, BYOD initiatives, and increasingly sophisticated cyber security threats.
Traditional security approaches were designed to protect the network perimeter by separating “trusted” from “untrusted” networks. In the campus network, these traditional security solutions are generally delivered by legacy Network Access Control (NAC), 802.1X, and VLAN products. The perimeter security approach they enforce assumes that users and devices within the corporate environment can be trusted. However, this assumption falls down in the face of common cyber threats, such as a compromised device or a user with stolen credentials who penetrates the network. In this case, an attacker has relatively easy access to a company’s privileged intranet to do things like move laterally, steal data, or deliver ransomware.
A Zero Trust approach on the other hand requires organizations to assume that their campus and branch networks are untrusted, and that a breach has either already occurred within the network or that it’s only a matter of time until it will. The Zero Trust security framework supports this approach by enforcing three core principles:
In a Zero Trust world, users and devices must be explicitly authenticated and authorized as trustworthy before being granted access. Access to resources should be granular at the application level, and granted based on the principle of least privilege, meaning that an entity is only given the minimum level of access necessary to perform their job. In addition, access is not “unconditional”, but rather is based on continuous monitoring of the device’s security posture, geographic location, and other contextual information. This means that if a device’s security posture should change, access could be revoked or limited. The result is that, with Zero Trust, compromised users and devices are much more restricted in their ability to move laterally or infect other devices due to their limited scope of access.
Today, as remote work evolves into “hybrid work”, many employees are returning to the office full time, or alternating between onsite and remote locations. According to a recent survey by Statista, 53% of U.S. workers reported working in a hybrid manner at the end of 2022.
Here’s the problem – most Zero Trust solutions today are cloud delivered. They are designed to protect REMOTE workers, but deactivate when the user is in an office. So when users come back to the office, they fall back under existing legacy perimeter-based security approaches.
But what about using cloud delivered Zero Trust services onsite? This approach generally runs into problems, for a number of reasons:
As a result, very few organizations have been able to achieve the vision of using a Zero Trust Network Access approach in an integrated fashion across their enterprise for all their users, whether remote or onsite.
Organizations that are looking for a holistic Zero Trust solution that can be applied across their enterprise for all their users need to expand their requirements. Some of these new requirements include:
What other requirements do you see for onsite ZTNA? Let me know at dmaier@versa-networks.com.
Versa Zero Trust Everywhere ™ is the industry’s first solution delivering Zero Trust security for both remote and on-premises users, with optimized user-to-application performance. Versa is expanding its portfolio with two new products to deliver Zero Trust Everywhere:
These two new components integrate seamlessly with Versa’s existing cloud-delivered ZTNA solution (Versa Secure Private Access) as well as our traffic-engineered cloud SASE fabric (Versa SASE Fabric) to deliver an integrated ZTNA solution across the enterprise, managed from a single policy repository and management plane.
For more information on Versa Zero Trust Everywhere, please:
Subscribe to the Versa Blog