
This blog captures a presentation delivered by Versa’s Chief Marketing Officer at RSAC 2025. Presented live at the Versa booth, it outlines why SASE is transforming enterprise security – and how Versa uniquely delivers on that transformation with its unified, AI-powered platform.
In today’s digital world, cybersecurity is a race against time. Every second counts, because threat actors are faster, more coordinated, and better funded than ever before.
And it would seem they’re winning – breaches are happening at an unprecedented scale. Just in the past year alone, UnitedHealth, AT&T, and the French government each suffered incidents that exposed tens of millions of records. Despite having poured more money into security, many organizations like these find themselves falling further behind. Why is this?
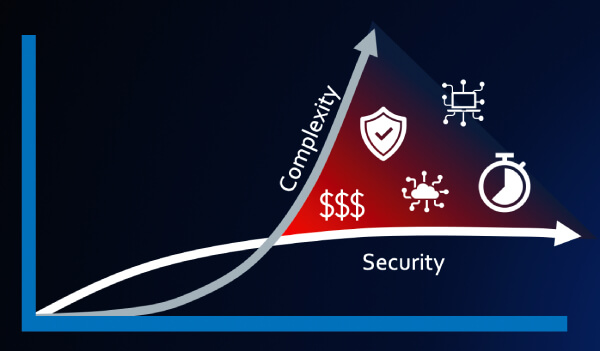
Fig. 1 – Diminishing returns in security effectiveness
Because the traditional model of cybersecurity – layering point solutions in a “defense-in-depth” strategy – is collapsing under its own weight.
For years, CISOs have built up layers of security around the enterprise, from the physical perimeter to the endpoint, to the application and the data. The idea was sound: multiple lines of defense reduce the risk of a single point of failure.
But in practice, this approach has morphed into “product sprawl” – a patchwork of disparate tools, vendors, consoles, and policy engines. Each product might do its job well, but together they create friction. Visibility gaps. Conflicting policies. Alert overload. Slow response times. Rising costs. And worst of all, reduced effectiveness.

Fig. 2 – Defense-in-depth has led to product sprawl
The fact is that we’re far past the point of diminishing returns with this model. It’s even more obvious when you consider how much the nature of enterprise computing has changed: the volume of data flowing through enterprise environments is exploding, the number of remote and hybrid users has surged, and applications are scattered across on-prem, SaaS, and multi-cloud. The attack surface has become too broad, and the traditional approach is simply too complex and too slow.
It’s time for a paradigm shift – we need to jump to a new “security curve.”
Secure Access Service Edge (SASE) isn’t just another acronym – it’s a fundamental shift in how we think about security architecture. It converges security and networking into a single, integrated cloud-delivered platform. When implemented correctly, SASE provides faster, more scalable, and more consistent protection than fragmented legacy approaches.
So what makes SASE platforms such a transformative force for security?
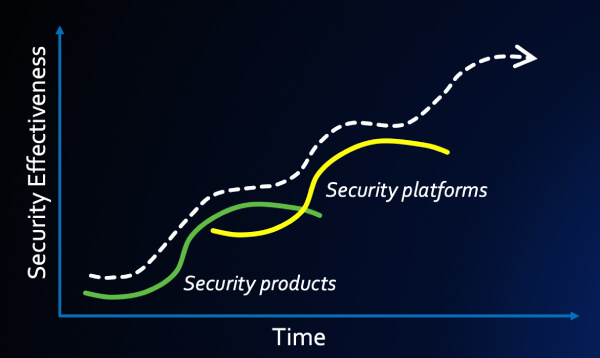
Fig. 3 – Security needs to jump to a new curve
Let’s explore the seven critical ways SASE reshapes enterprise security from the ground up.
In legacy architectures, security and networking are built and operated separately. Firewalls, SWGs, VPNs, and CASBs sit apart from routers, SD-WAN controllers, and WAN optimizers. Each tool has its own policy engine and data flow – and stitching them together is complex and fragile.
SASE eliminates this divide by unifying these functions. Instead of “hop-by-hop” inspection service chained across multiple appliances, security is applied natively within the flow of traffic, alongside routing and policy enforcement. This streamlines operations, reduces latency, and closes gaps between teams.
With traditional tools, security teams suffer from “swivel-chair management” – jumping from one interface to another, trying to make sense of incomplete, delayed, or contradictory data.
SASE gives security and networking teams a unified control plane. You gain full visibility into users, devices, applications, and threats across the entire infrastructure – from branch to cloud to remote endpoints. Correlation becomes faster. Context becomes richer. And response becomes real-time.
Legacy security architectures often depend on multiple disconnected tools that analyze logs or telemetry out-of-band and then pass alerts to other systems for enforcement. This multi-hop model introduces delays and creates brittle dependencies—leaving critical gaps where threats can slip through or responses can fail.
SASE solves this by enforcing security policies inline, directly in the traffic path. This enables immediate, coordinated action—blocking malicious URLs, stopping data exfiltration, or terminating risky sessions in real time. By eliminating lag and reducing reliance on fragile toolchains, SASE delivers faster, more reliable protection.
Of course defense-in-depth isn’t dead – it’s evolving. SASE provides all the core pillars of layered security (firewall, intrusion prevention, DLP, SWG, CASB, ZTNA, etc.), but delivers them as coordinated capabilities in a single architecture.
The value of delivering defense-in-depth capabilities within a single architecture lies in cohesive, layered protection without the operational burden of stitching together multiple point solutions. When security functions like ZTNA, SWG, NGFW, IPS, and threat intelligence operate within one platform, they share context, enforce unified policies, and respond to threats in real time. This approach reduces gaps, eliminates redundancy, and simplifies management—strengthening security posture while improving performance and efficiency.
In a hybrid world, users are constantly moving about and connecting from anywhere – home, HQ, branch, coffee shop – and access applications across SaaS, private data centers, and cloud. With legacy tools, policies may only apply in certain locations or depend on whether traffic is routed through the “corporate perimeter.”
SASE ensures uniform policy enforcement across any and all locations, devices, and networks. Identity, posture, application, and content policies are applied everywhere, in real time. This consistency dramatically reduces risk and simplifies compliance.
The Zero Trust philosophy – “never trust, always verify” – is critical in today’s evolving threat landscape. Yet many organizations limit ZTNA to remote users, while relying on traditional NAC for in-office authentication. This creates uneven security coverage and leaves gaps where trust is assumed after initial access.
SASE platforms like Versa embed Zero Trust principles across all users, locations, and traffic. Device posture is continuously evaluated, least-privilege access is dynamically enforced, and identity-aware routing with microsegmentation limits lateral movement. All policies are centrally managed and auditable—ensuring consistent, adaptive protection everywhere.
Finally, SASE lays the foundation for AI-driven security by generating contextually rich, consistent, and real-time data across all users, devices, and locations. Unlike fragmented, normalized logs pulled from a patchwork of point products, SASE platforms like Versa produce AI-ready data natively – eliminating blind spots and enabling deeper, more accurate analysis.
This unified data model empowers machine learning to detect anomalies, prioritize threats, reduce alert fatigue, and automate responses. The result is not just faster detection—it’s intelligent, adaptive decision-making at machine speed, allowing your security posture to evolve as fast as the threats themselves.
Not all SASE platforms are created equal. Some vendors offer a collection of loosely integrated tools acquired over time, stitched together via APIs. These “platformized” solutions often carry the same baggage as legacy systems – complexity, inconsistency, and slow performance.
At Versa, we’ve taken a fundamentally different approach. Our VersaONE Universal SASE Platform is built from the ground up as a unified system built on a single software stack – purpose-built to deliver secure, high-performance networking with fully integrated security.
Here’s what makes Versa unique:
VersaONE combines SD-WAN, NGFW, ZTNA, SWG, CASB, DLP, IDS/IPS, and advanced threat protection into a single-pass architecture. That means traffic is inspected, routed, and secured in one seamless process—reducing latency, conserving bandwidth, and simplifying operations.
There’s no need for separate security appliances, no backhauling, and no patchwork of point solutions. Just one platform, one OS, one policy engine.
With Versa, security isn’t an afterthought – it’s embedded into the core of the platform. Every flow is authenticated, every user is verified, every packet is inspected. Whether you’re connecting from a branch, a remote location, or a mobile device, the same security posture follows you.
That means no gaps. No exceptions. No trade-offs between performance and protection.
Versa’s integrated analytics engine ingests data across the entire platform – network, user behavior, threat intel, application access – and applies AI reasoning and machine learning to surface what matters most. Whether you’re identifying a rogue insider, a misconfigured policy, or a zero-day exploit, Versa helps you act faster and smarter.
And it doesn’t stop at detection. With automation and policy enforcement built in, Versa enables rapid response to emerging threats – without human delay.
Versa’s platform is designed to meet customers where they are. Whether you need a cloud-delivered SASE-as-a-Service, a Private SASE instance for dedicated control, or a Sovereign SASE model for regulatory compliance and data residency, Versa supports all deployment models – on the same codebase, with the same capabilities.
This flexibility is critical for multinational enterprises, public sector agencies, and service providers alike.
Security leaders are right to feel overwhelmed. The threat landscape is evolving faster than ever. Legacy tools are failing to keep up. And the pressure to consolidate, simplify, and modernize has never been greater.
But SASE offers a way forward – a new architecture that’s faster, smarter, and built for how businesses operate today.
At Versa, we believe the time for transformation is now. Our platform doesn’t just promise SASE – it delivers it. With VersaONE, you get true convergence, intelligent enforcement, and AI-powered protection that moves at the speed of modern threats.
If you’re ready to break free from the limits of legacy defense-in-depth and embrace a smarter, unified future, we’re ready to help.
Subscribe to the Versa Blog