
Multi-tenancy for an enterprise? It’s a service provider thing! No, not really, in the e-commerce age you need it more than ever. There are myriad reasons to secure your enterprise network with a genuine multi-tenancy architecture—it’s critical to plug the security deficits of the also-ran legacy tenancy architectures.
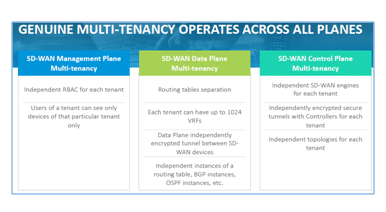
Listen to this webinar to hear Neil Danilowicz, Principal Architect, and myself, discuss the essentials of a genuine multi-tenancy architecture: the complete isolation of the control, data and management planes. If any of these planes bleeds across—in a shared device; in shared access to any network resource—it opens a security vulnerability. Enterprises use this total segmentation to comply with regulations such as PCI DSS, HIPAA and GDPR. And also to integrate mergers and acquisitions; separate engineering from sales or supply chain or legal organizations; protect business units; contain failure and broadcast domains.
When we all commuted to work in brick-and-mortar offices (remember that?), the internal enterprise network could be readily shielded from the outside world. Internet access was either denied altogether, or allowed in only one single place: behind a beefy firewall in the data center. But with the transformation of the digital economy, trends in mobility, Internet access everywhere—often the only viable choice for smaller or temporary sites, IoT-based tracking and monitoring, cloud-based computing and resources, and work-from-home on a scale previously unimaginable, your business thrives on the very fuel of its connections to everywhere and everyone. It’s a different world, it needs a different solution.
To deploy a truly secure architecture, it is imperative that the management, control and data planes are completely separated: in access, transport, resources, encryption methods, and authentication. The weakest link of a shared resource determines how well your multi-tenancy works. Get a Secure SD-WAN solution today.
Subscribe to the Versa Blog