
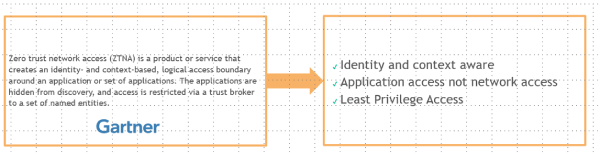
Zero Trust Network Access (ZTNA), also referred to as Software Defined Perimeter (SDP), was coined by Gartner in 2019 to describe products and services which enables secure connections to private applications centered on Zero Trust Model. Gartner defines Zero Trust Network Access as “a product or service that creates an identity and context-based, logical access boundary around an application or set of applications. The applications are hidden from discovery, and access is restricted via a trust broker to a set of named entities.”
With the dissolution of the traditional security perimeter, increased proliferation of SaaS applications, increased migration of workloads to public cloud, dramatic increase in remote work force made necessary due to COVID-19 coupled with increased adoption of BYOD policies in most enterprises have altered the threat landscape dramatically. This has triggered the need for implementing a zero-trust security framework to enable enterprises to provide secure access to private applications and SaaS applications using a zero-trust model.
As per the initial SASE framework, which was published by Gartner in 2019, Zero Trust Network Access is one of the Core components of the Secure Access Services Edge and hence almost all the SASE Vendors specifically Secure Services Edge Vendors offer, ZTNA as a service as a part of their overall SSE solution from their cloud hosted gateways.
Zero trust was first conceptualized by Forrester Analyst John Kindervarg in the year 2010. Zero Trust as defined by Gartner is a simplified way of describing an approach where implicit trust is removed from all computing Infrastructure. Zero trust is a way of thinking, not a specific technology or architecture. It’s about zero implicit trust, as that’s what customers want to get rid of.” In more simple terms, Zero Trust can be defined as “Never Trust Always Verify“.
Zero Trust is based on 3 fundamental principles as illustrated in the diagram below:
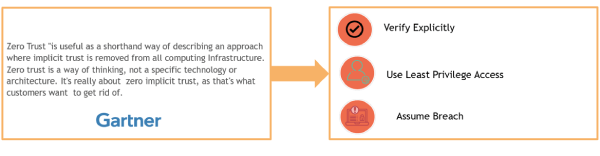
Most of the present ZTNA solutions available today to adhere to the principles of Zero Trust at a minimum, try to implement the following verification capabilities in their product:
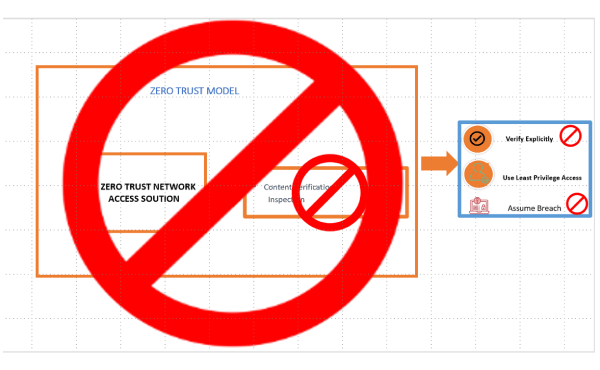
However, most of the present ZTNA solutions fail to address the below capabiliities:
In cases where the Device Identity cannot be verified, the ZTNA solution relies on only the User Identity to establish the trust. This is a weak security posture, because the ZTNA solution does not offer adequate security protection, in case of compromised user credentials, or when unmanaged or BYOD devices are used to access corporate resources or private applications of the enterprise. A ZTNA solution that incorporates Device Authentication, Device Fingerprinting and Device Posture Checks offers the strongest security posture when providing private access to enterprise applications and resources.
Any ZTNA Solution that doesn’t provide “Full L7 Content inspection” capabilties isn’t really Zero Trust in the true sense since it ends up violating the following 2 core principles of Zero Trust Model.
Therefore, in conclusion any ZTNA Solution which doesn’t offer Device Authentication or full security inspection capabilities for Private Access Traffic cannot be termed as Zero Trust in the true sense. At best, they can be referred to as “Private Access/Remote Access Solutions with partial Zero Trust Capabilities”. Unfortunately, most of the ZTNA solutions which are offered by the existing SASE/SSE Vendors fall into this category since they offer either very limited Device Posture checks and security inspection or no security inspection capabilities for Private Access traffic.
As a customer to evaluate whether any ZTNA solution which you may have implemented/shortlisted, all you will need answer to these 4 fundamental questions:
Versa Secure Access is a true Zero Trust ZTNA solution that enables customers to give secure remote access to their private applications for their remote workforce while ensuring that it confirms to all the 3 basic tenants of Zero Trust.
Versa Secure Access is one of the core components of Versa Unified SASE and is delivered as a service from Versa Hosted Cloud Gateways.
Hit the Contact Us and drop us a line. We will get you in touch with a security expert to brief you how VERSA SECURE ACCESS can help you provide Secure Remote Access to your applications while adhering to the Zero Trust Model.
Subscribe to the Versa Blog