
Whether private or custom apps live in data centers or span across multiple clouds, ZTNA for private applications helps to make them “invisible” to the outside world, reducing the attack surface. But it’s important to maintain visibility for your own security teams. Critical context—like who’s accessing what, whether policies are working as expected, or if a threat can move laterally across your environment-are important to maintain the ongoing security posture and truly secure private apps. You need more than access control—you need visibility first.
A few simple examples help to highlight the challenges when securing private apps:
When a user accesses an unauthorized private application, or an app quietly breaks segmentation rules, it’s not just a one-off mistake—it’s a symptom. A symptom of trust boundaries that aren’t clearly defined with static access controls that don’t adjust as roles, apps, or risks change and lack of visibility into what applications actually do after access is granted. Without fixing these blind spots, private apps stay vulnerable—regardless of how hidden they appear on the surface.
A visibility-driven approach is needed to see what’s happening within your private application estate — across users, devices, and services as a single entity.

Figure 1: Visibility-first Approach
To truly protect private applications, ZTNA needs to go beyond simply granting or denying access. Preventing lateral movement and closing compliance gaps requires continuous awareness of what’s happening inside your environment. A visibility-driven approach to ZTNA should give you clear insight into:
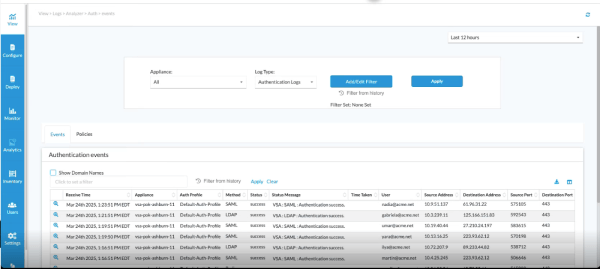
Figure 2: Continuous awareness of what’s happening inside your environment
This will ensure segmentation integrity and provide evidence-based reporting—critical for proving compliance.
Versa’s VSPA platform brings Zero Trust access to private applications without sacrificing visibility or scalability. It delivers private access without tunnel-based opacity or policy fragmentation. It enforces identity verification and policy at every access request—ensuring secure, observable, and compliant private connectivity without compromising user experience. It’s built to ensure lateral controls, visibility, and continuous compliance across cloud and on-premises private applications with following:
App-Aware Overlay with Full Visibility and Telemetry
With Versa VSPA, each user’s session is steered through context-aware service edges, with:
East-West Visibility and Segmentation
As part of Versa Zero Trust Everywhere, the platform monitors and controls east-west flows between private applications, users, and environments:
This ensures threats don’t move laterally once initial access is gained.
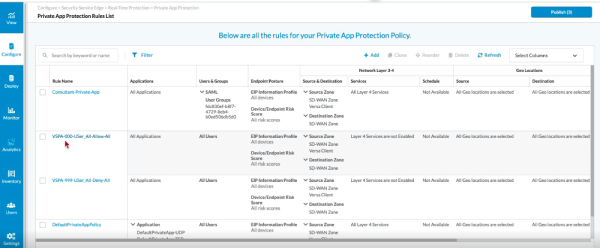
Figure 3: ZTNA Policy Enforcement
Identity & Risk-Aware Policy Enforcement
VSPA doesn’t rely solely on static policies or identity verification at connection time. It continuously evaluates risk posture with built-in behavioral analytics:
Combined with Versa’s integrated UEBA engine, this allows for adaptive security risk postures to be enforced in real time.
Integrated Security Stack
VSPA is part of Versa’s Unified SASE platform, that provides visibility and policy enforcement for other security pillars too as following:
Single-Pass Architecture for Aggregated and Corelated Data:
Unlike few ZTNA platforms where traffic is decrypted, analyzed, then re-encrypted across multiple point security solutions (e.g., SWG → ZTNA → FWaaS), Versa SSE uses a single-pass parallel processing pipeline. Traffic is:
Reducing the attack surface for private applications requires more than network access control—it demands deep, continuous visibility. Versa VSPA delivers a visibility-first ZTNA model that prevents lateral movement, enforces identity-aware segmentation, and ensures compliance across your internal environments. With integrated security and single-pass enforcement, VSPA transforms private access into a fully governed, observable, and secure service.
Discover how Versa VSPA can secure your private applications with zero trust and full visibility. To get started with 90-day Try and Buy offer, schedule a 30-min call with an expert here.
Subscribe to the Versa Blog