
After several weeks of quiet, especially during the Christmas holidays, the Emotet malware bot is up and running again, and it seems stronger and smarter. Several IT security firms have reported seeing phishing emails delivering Emotet via malicious Word documents and even delayed holiday e-greetings. Cyber-attackers using Emotet seem to have used this brief hiatus to improve the malware’s social engineering abilities, with almost a fourth of infected emails being sent as replies to existing email threads.
Designed initially as a banking malware, the Emotet Trojan was first identified by security researchers in 2014. The malware delivery botnet spreads itself by accessing the email services of infected computers and then uses this access to send phishing emails to the target’s contacts by replying to previous email threads, and sometimes adding the target’s name to the subject line of the email. This is an effective tactic, because the target sees the email coming from a trusted contact, easily bypassing security filters.
The U.S. Computer Emergency Response Team (US-CERT) calls Emotet “the most costly and destructive malware” on the Internet. Infection usually begins with a user being sent a phishing e-mail containing a malicious Word document or a link to a malicious URL that will download a maldoc upon clicking. Upon opening the malicious document, a combination of obfuscated VBA scripts / macros instructs the target machine to download a remote payload consisting of a number of different modules.
Emotet is easily able to get under the radar and avoid detection by anti-malware software. It works by using worm-like capabilities to help spread to other connected computers. Such abilities have made Emotet one of the most expensive and destructive malware, affecting government and private sectors, individuals and organizations, and costing upwards of USD 1 Million per incident to clean up. Over the years Emotet has been stealing banking logins, financial data, and even Bitcoin wallets. It also acts a loader to deliver other payloads like Trickbot and Ryuk ransomware, triggering a whole security campaign to tackle the threats posed by the “unholy alliance” of the three.
Emotet spreads through spam emails either via malicious script, macro-enabled document files, or malicious links. Emotet plunders your contacts list and sends itself to your friends, family, coworkers etc. Since these emails are being sent out from your email account, they look less like spam and the recipients are more inclined to click the URLs or download infected files. Emotet emails dupe users because they typically contain familiar branding designed to look like a legitimate email, and uses file names like “Your Invoice” or “Payment Details” that compel users to click the malicious files. If there is connected network, Emotet spreads using a list of common passwords, guessing its way into other connected computers in a brute-force attack. Here’s a good description of how Emotet infects a file.
Emotet has a number of tricks to avoid detection and analysis. It is polymorphic, which means it can change itself every time it is downloaded to evade signature-based detection. What’s scary is that Emotet also uses C&C servers to receive updates, which work in the same way as the target’s OS updates. This allows Emotet to work undetected without any outward signs, and the attackers can install updated versions of the software, install additional malware, or use the system as a dumping ground for stolen data such as financial credentials, login data and email addresses.
Emotet, a botnet malware loader, enters the system via malicious document that runs a VBA script and loads a powershell script which downloads Emotet loader into a system. Emotet then communicates with the C&C to upgrade itself as well download other modules. All these downloads are detected by our AV module and rejected. The secondary payloads like Trickbot generate SMB traffic in its attempt to infect other systems in the network. These trigger the IPS signatures related to SMB traffic and prevent further infection. Versa is able to thwart the infection at different stages of the infection lifecycle.
Versa AV detects Emotet malicious documents that start the infections as well as the executables that are downloaded during infections. It also detects the secondary payload of Trickbot.
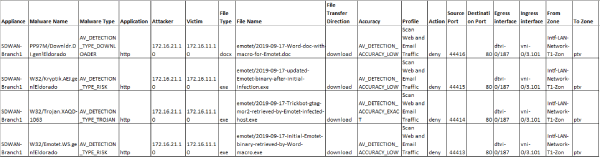
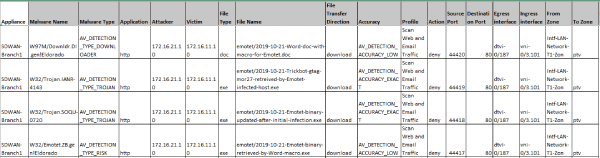
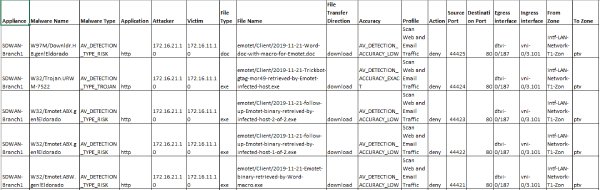
Fig: Emotet and components detected by Versa AV
We also get IPS detection for the Trickbot AD infection which is the secondary payload dropped by emotet infection in S3 campaign. It detects the SMB traffic that the malware uses to infect the other systems in the network.
The following signatures are hit using the versa Recommended profile in the IPS module.:
Microsoft Windows SMB Server SMBv1 CVE-2017-0147 Information Disclosure -> CVE-2017-0147
Microsoft Windows SMB-DS Trans Max Param OS-WINDOWS attempt -> CVE-2005-1206
Sun Directory Server LDAP denial of service attempt -> CVE-2006-0647
Microsoft Windows SMB-DS Trans Max Param/Count OS-WINDOWS attempt -> CVE-2002-0724
NETBIOS SMB-DS NT Trans Secondary Param Count overflow attempt -> CVE-2003-0085
The good news is that Emotet spreads more easily if the end-user is unsuspecting or careless. If you can be vigilant and take the precautions listed below, you can easily check an Emotet attack and nip it in the bud.
Emotet is one of the most dangerous threats facing enterprises today, and its revival is not a good sign. Users and security teams should be particularly vigilant of the botnet’s ability to reply to existing email threads. New-school security awareness training can help employees stay up-to-date and know what to watch out for.
Post the “Emotet hiatus”, we have observed a large amount of change in both the cosmetic appearance and the underlying structure of different Emotet components, all aimed at increasing the efficacy of its tools and attacks. It also seems more adept at evading or breaking analysis techniques and tools that were previously able to obstruct its TTPs.
While we don’t know what the future holds in regards to Emotet, what’s certain is that IT teams need to be clear and prepared to battle any new retooling or techniques that might emerge. The old adage of prevention being better than cure has perhaps never held more weight than in safeguarding your organization from this malicious botnet.
Subscribe to the Versa Blog