
Remote and hybrid work changed enterprise risk forever. The network is no longer a physical perimeter, yet traditional VPN architectures still operate as if it is. Once a VPN connection is granted, attackers gain broad access and freedom to move laterally with very few barriers. That exposure is no longer acceptable.
Organizations now operate with distributed workforces, SaaS adoption, and hybrid cloud environments. Legacy VPNs cannot keep up. Attackers exploit stolen credentials, unpatched gateways, and implicit trust to bypass defenses and reach high-value systems.
The Structural Risks of VPN Architectures
VPNs introduce inherent weaknesses that can be exploited.
Modern access needs consistent Zero Trust security across cloud, data center, and branch — enforced at application-level granularity and continuously validated.
Selecting Right ZTNA Architecture
Many ZTNA solutions focus only on initial access decisions and lack the inline inspection or segmentation needed to stop advanced threats.
Enterprises need ZTNA that:
A Zero Trust approach must protect users wherever they are, not just broker connections.
Versa’s Unified Approach to Zero Trust Access
Versa Zero Trust Network Access is delivered through a unified SASE platform where connectivity and security are architected together. This removes the need to bolt on inspection or maintain separate cloud brokers.
Versa enforces identity, user posture, device posture, and context-based access to specific applications with full inline threat prevention and deep visibility. Traffic is secured using standards-based TLS/DTLS/IPsec and tunneled directly to Versa gateways from endpoints or data center VNFs, enabling inline inspection without additional infrastructure with following:
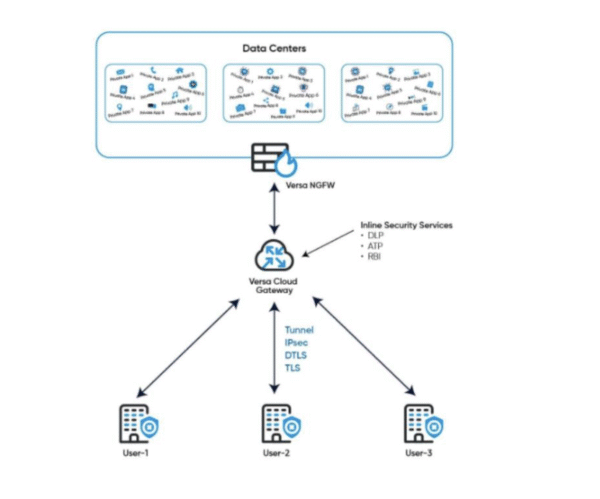
Customers can also leverage existing Versa CPEs or third-party firewalls for local connectivity. The architecture is built for global scale, high performance, and simplified operations from the start.
Key Advantages
Versa builds Zero Trust into the connectivity fabric itself, enabling secure access that operates at the speed of business.
Strategic Advantages for the Enterprise
Zero Trust access is not only a security win. It simplifies operations, restores visibility, and improves user experience across every location and provides following:
Stronger ransomware defense
Inline threat inspection and granular access sharply reduce the blast radius of compromise. Even if credentials are stolen, attackers cannot traverse networks or reach sensitive workloads.
East-West segmentation inside the data center
ZTNA controls apply not only to users entering the network but also to traffic between workloads. Internal movement is validated and inspected to prevent infiltration from escalating silently over time.
Linear scalability without connector sprawl
No more standing up dozens of bespoke brokers across cloud and DC sites. A single scalable fabric reduces cost while delivering consistent protection across thousands of apps.
Standards-aligned Zero Trust architecture
Compliance initiatives accelerate because Versa maps directly to NIST 800-207 and similar frameworks. Using widely adopted encryption and identity standards simplifies audits and trust validation.
Future-ready design
As the business adopts new SaaS, expands globally, or modernizes infrastructure, policies and protections expand automatically with it. There’s no architecture refresh required to stay secure.
VPN architectures were never built for a world without perimeters. Versa ZTNA eliminates implicit trust and enforces Zero Trust principles consistently everywhere users connect and applications run.
Ready to move beyond legacy VPNs? Explore how Versa Zero Trust Network Access (ZTNA) compared to other ZTNA solution delivers identity-driven, secure connectivity for every user, device, and application — anywhere they connect.
Subscribe to the Versa Blog