
Storm-0978 (by other means as RomCom) is a Russian-based Cybercriminal group known for conducting ransomware and extortion-only operations, as well as credential stealing targeting attacks. Storm-0978 operates, develops, and distributes the RomCom backdoor. The actor’s latest campaign detected in June 2023 involved abuse of CVE-2023-36884 to deliver a backdoor with similarities to RomCom. Storm-0978’s targeted operations impacted government and military organizations primarily in Ukraine, as well as organizations in Europe and North America that may be involved in Ukrainian affairs.
Microsoft’s Patch Tuesday for 11-July-23 unveiled i132 vulnerabilities. Additionally, Microsoft has published a dedicated article addressing CVE-2023-36884, an Office and Windows HTML Remote Code Execution vulnerability that attempts to exploit this vulnerability using specially crafted Microsoft Office documents.
Storm-0978 uses trojanized versions of popular, legitimate software. Observed examples of trojanized software are multiple Adobe products, Advanced IP Scanner, Solarwinds Network Performance Monitor, Solarwinds Orion, KeePass, and Signal. In order to provide the trojanized installers for deployment, Storm-0978 typically registers malicious domains that mimic the legitimate software.
In financially motivated attacks involving ransomware, Storm-0978 has been observed using the Industrial Spy ransomware, a ransomware strain first observed in the wild in May 2022, and the Underground ransomware. The actor has also used the Trigona ransomware in at least one identified attack.
Storm-0978 has acquired multiple exploits targeting zero-day vulnerabilities from actors on the dark net. Exploit activities include abuse of CVE-2023-36884, which is a remote code execution vulnerability via identified in Microsoft Word documents in June 2023, as well as abuse of vulnerabilities contributing to a security feature bypass of Office Applications.
Storm-0978 initiated a series of phishing campaigns by establishing fraudulent websites that resembled authentic software installers. In December 2022, Storm-0978 gained unauthorized access to an email account that belonged to the Ukrainian Ministry of Defense. CERT-UA released a report which warned Ukrainian military personnel of the malware attack. A compromised Ukrainian Ministry of Defense email account was found sending phishing emails and instant messages to users of the ‘DELTA’ situational awareness program to infect systems with information-stealing malware. DELTA is an intelligence collection and management system created by Ukraine with the help of its allies to help the military track the movements of enemy forces.
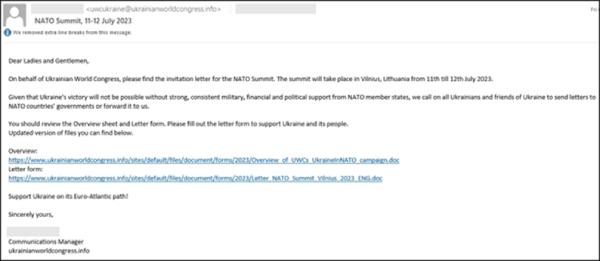
In June 2023 a new phishing campaign attributed to Storm-0978 was established by the Underground Team. The below figure shows the phishing email used by Storm-0978 to exploit the vulnerability CVE-2023-36884.
In addition to phishing attacks, Storm-0978 has also been observed using more sophisticated password cracking attacks targeting Ukraine. Storm-0978 has gained access to credentials by extracting password hashes from the Security Account Manager (SAM) through the Windows registry. Subsequently, Storm-0978 has employed the SMBExec and WMIExec functionalities of the Impacket framework for lateral movement within the compromised systems. While this technique was not used in Storm-0978’s original exploit of CVE-2023-36884, the password extraction code is included in the backdoor trojan delivered by the phishing attack. Security researchers have theorized that this is pre-loaded code that will be activated as part of the next variant of the attack.
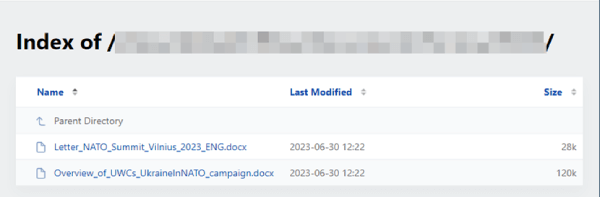
The figure 2 and Figure 3 below (Source: Microsoft and cyble) displays the MS Word document utilized throughout the campaign, specifically designed to align with the NATO Summit.

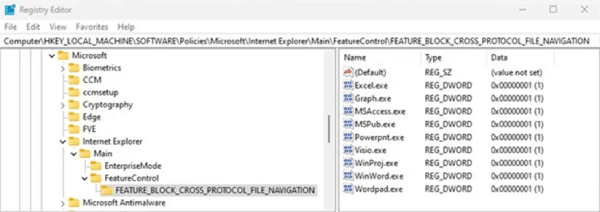
To mitigate this attack that leverages CVE-2023-36884, Microsoft recommends:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-36884
Subscribe to the Versa Blog