
This blog shows how bringing LLM-powered automation into policy management helps security and networking teams build, audit, and optimize network policies more efficiently. It integrates into existing workflows, offering real-time access to current configurations and intelligent policy insights — all without requiring teams to switch tools.
During RSA 2025, we announced the Versa MCP Server — a powerful utility that connects the Versa Unified SASE platform with leading Agentic AI tools such as Claude, ChatGPT, Gemini, and Microsoft Copilot. By securely exposing Versa APIs — an integration that can also be leveraged with on-prem LLMs — the MCP Server enables LLM-powered agents to query Versa deployments in real time, providing dynamic access to network and security data. For NetOps and SecOps teams, this means faster incident resolution, greater visibility into configurations and outcomes, and significantly less manual overhead.
Building on the foundation of the MCP Server, this blog demonstrates how it can be used to access, configure, and enforce secure access client policies more intelligently and effectively. The utility tackles a persistent operational challenge: fragmented policy management spread across dashboards, consoles, and chat interfaces. By centralizing policy visibility and applying LLM-powered analysis, it enables engineers to build, validate, and refine rules with greater speed and confidence. Key capabilities for managing Secure Access Client (SAC) rules include:
Let’s walk through a real-world scenario where the MCP Configuration Tool is used to create and delete a SAC rule. For this example, we will use Claude Desktop to interact with the MCP Server.
We begin by cloning the MCP server repository and following the setup instructions in the README.md. Once installed, check or modify the claude_desktop_config.json file for Claude Desktop to ensure it includes the necessary Versa MCP servers/tools. A sample is shown below:
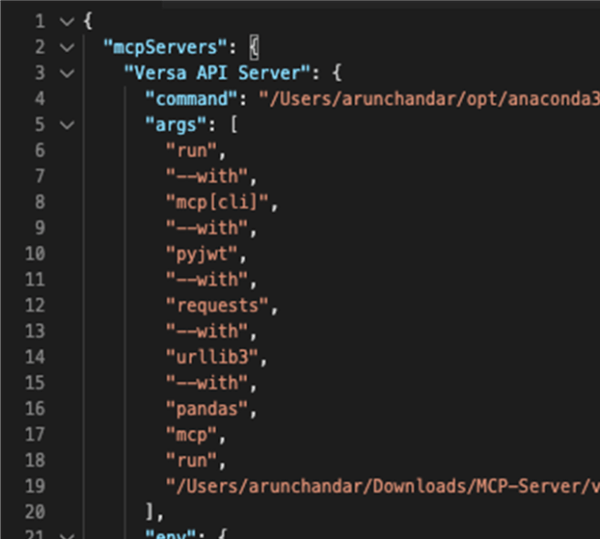
Note:
Once complete, proceed to Step 2.
Next, launch Claude Desktop and confirm that it successfully connects to the MCP Server. Upon startup, the configuration panel displays all active integrations — including the Versa API Server if the connection is established.
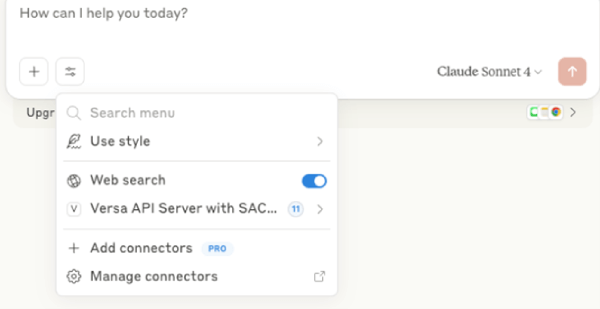
From this panel, available tools can be reviewed and toggled on or off as needed.
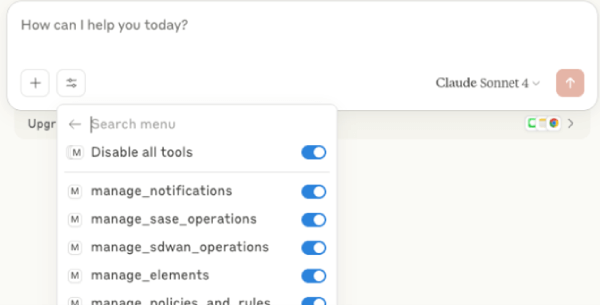
Next, we use Claude Desktop to define a new Secure Access Client (SAC) rule. In this case, the goal is to create a policy that applies specifically to Windows 10 devices used by a specific user.
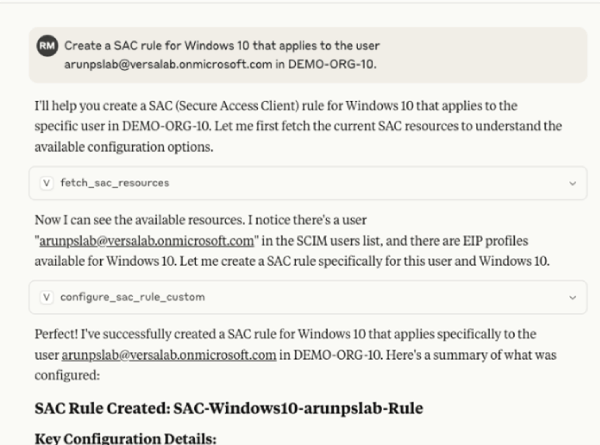
To confirm the rule was applied correctly, log into Versa Concerto and navigate to the SAC policy configuration page. There, we verify that the new rule — scoped to Windows 10 and the specific user — appears in the active policy list.

To remove the previously created SAC rule, we issue a prompt in Claude Desktop requesting its deletion.
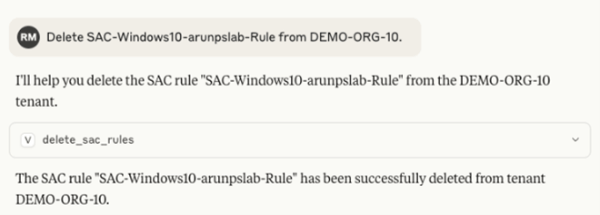
This example illustrates how the MCP Server simplifies and strengthens secure access policy management by combining real-time data with LLM-powered insights. It allows teams to build cleaner, more secure policies — faster and with significantly less manual effort. For a full walkthrough of the tool in action, including a complete scenario demonstrated here, check out the demo video here.
Learn more about SASE use cases for MCP Servers here.
Subscribe to the Versa Blog