
Domain Name System (DNS), the system that translates domain names into IP addresses, is one of the most foundational parts of the internet. It’s also one of the least inspected by traditional security tools. Now, attackers are taking advantage of this oversight to use it as a cover channel to deliver malware.
A recent Ars Technica article uncovered a sophisticated campaign where hackers embedded malware inside DNS TXT records. These records, typically used for harmless tasks like domain verification or email authentication, were repurposed to store chunks of malicious code.
In this campaign, malware was first converted into hexadecimal format and split into hundreds of small chunks. The attackers then registered a domain, whitetreecollective[.]com, and created hundreds of subdomains. Each chunk of malware was then stored in the TXT record of one of the subdomains. Once an attacker gains access to a network, the malware could be reassembled by making a series of DNS requests to these subdomains. Since DNS request traffic is both routine and rarely inspected, this method would allow the attackers to bypass traditional security tools.
DNS has often been used for covert channels and data exfiltration via tunneling, but hosting full malware payloads in DNS records is a more brazen and novel tactic. It underlines the need for DNS-level visibility and enforcement as part of a modern enterprise security strategy.
Versa’s approach to DNS security is designed to detect these kinds of evolving attacks. Part of the Versa Unified SASE platform and delivered through its Secure Web Gateway (SWG), Versa DNS Security is a fully integrated, cloud-delivered service that combines DNS filtering, reputation analysis, behavioral detection, and integration with broader security layers.
Specifically, Versa’s DNS security works across multiple dimensions to:
This layered approach ensures that threats hiding in DNS traffic are identified and stopped as early as possible.
Let’s take a closer look at how Versa can directly address the tactics used in this and similar DNS-based attacks.
Attackers using DNS records to host malware and malicious scripts is not a new behavior, and Versa is well versed in detecting and stopping these threats. Versa’s multiple security layers work together to prevent the use of DNS records for attacks though a combination of reputation and behavioral analysis:
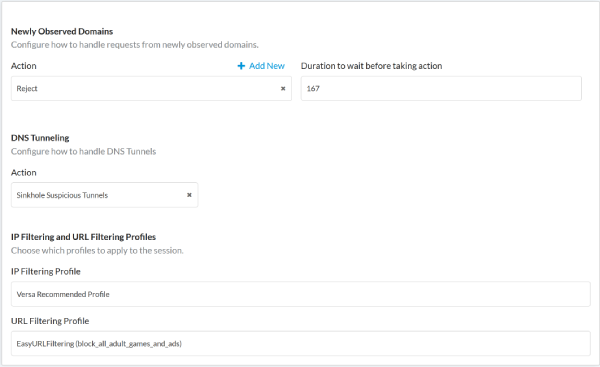
Figure 1: Versa supports multiple options and profiles to granularly configure DNS security.
In the Ars Technica article, instead of directly hosting malware in the DNS TXT field, the attackers added a new layer of subterfuge by encoding the malware file into hexadecimal format and breaking it up into chunks. Attackers often use TXT records to hide payloads because these records can store arbitrary text. While Versa doesn’t inspect every TXT record’s content directly, it provides powerful controls to block risky requests:
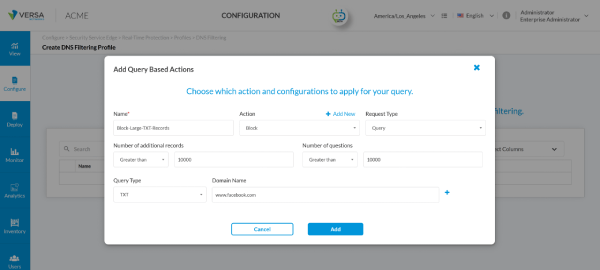
Figure 2. Query-based controls allow admins to block large or suspicious query volumes.
This means that even if malware is encoded and hidden inside a TXT record, Versa can prevent the malware from infecting the victim network.
These security innovations were spearheaded by a trio of Versa’s most creative technical minds who brought to the table deep domain expertise in mobile network architectures and a history of experience leading mobile core network and IoT product innovation at places like Juniper Networks, Cisco, and Alcatel-Lucent. The team leaders included Apurva Mehta, Versa’s co-founder and CTO; Rahul Vaidya, who leads product management in this area; and Chitresh Yadav, currently head of sales engineering and formerly head of Versa’s R&D lab.
We also have multiple additional filings pending, covering expanded use cases in both mobile and fixed-access scenarios.
DNS tunneling is a technique that hides data or communication inside DNS queries and responses to bypass security and/or exfiltrate information from a network. In the article, the attackers attempted to use DNS tunneling to transfer malware from a command-and-control (CnC) server (whitetreecollective[.]com) into a network. The behavior observed — frequent, repetitive requests to a single domain or its subdomains — is one characteristic of DNS tunneling.
Versa DNS Security is specifically designed to detect DNS tunneling and block CnC server communication through:
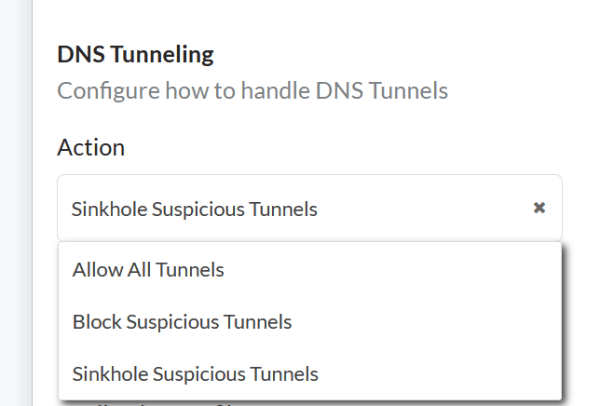
Figure 3. Easily configure how DNS tunneling detection should be handled.
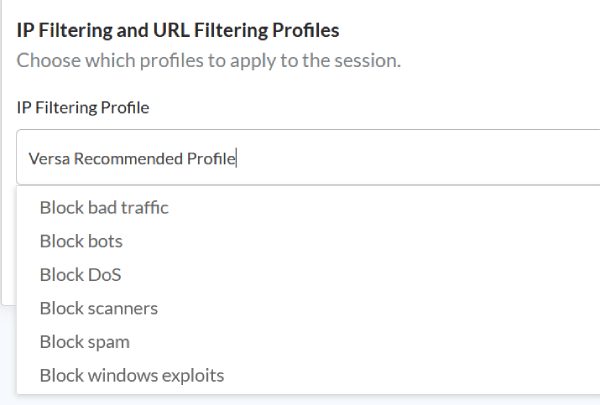
Figure 4. Versa supports user-defined and predefined profiles (like “Versa Recommended Profile”) for flexibility and ease of configuration.
Versa is highly effective at detecting these and other sophisticated security threats. To see how Versa performs in real-world threat detection, check out the out the CyberRatings.org 2025 Comparative Test Report: Security Service Edge (SSE).
Attackers will continue to exploit overlooked infrastructure like DNS to deliver malware and exfiltrate data. Versa’s multi-layered protections form a robust defense against sophisticated DNS-based attacks. By applying real-time inspection, behavioral analytics, and integrated filtering, Versa DNS Security can identify, block, and neutralize threats well before they reach the user or the network.
To learn how Versa’s DNS Security and other Security Service Edge products can help protect your organization from these and other novel attacks, schedule a demo with our team today.
Subscribe to the Versa Blog