
This security bulletin focuses on understanding the sophisticated exploitation of critical n-day and zero-day vulnerabilities in VPN and other network devices by state-sponsored threat actors, reinforcing the urgency for organizations to prioritize patching vulnerabilities in appliances known to be targeted. The recent exploitation of the critical FortiOS vulnerability followed a disclosure by CISA and other federal agencies revealing that China-linked threat group Volt Typhoon has been known to exploit network appliances from several vendors including Fortinet. Fortinet released a blog post to coincide with the U.S. agencies’ advisory, which pointed to “the need for organizations to have a robust patch management program in place and to follow best practices to ensure a secure infrastructure.” Other vendors named as frequent Volt Typhoon targets were Ivanti — whose Connect Secure VPN devices have seen widespread exploitation by attackers over the past month — as well as Cisco, NetGear and Citrix.
In recent years, the cyber threat landscape has evolved dramatically, with Volt Typhoon, also known as Insidious Taurus, emerging as a significant concern. Believed to be state-sponsored by the People’s Republic of China (PRC), this group’s sophisticated cyber-attacks on critical infrastructure across the United States have put security agencies on high alert.
Volt Typhoon has focused its efforts on infiltrating a wide range of critical infrastructure sectors such as:
The primary concern with Volt Typhoon lies in their ability to pre-position themselves within critical networks. This positioning could enable them to execute disruptive actions, especially in the context of heightened geopolitical tensions. The potential for such disruptions poses a significant risk not only to the immediate functionality of critical services but also to national security and economic stability.
In light of the threat posed by Volt Typhoon, US cybersecurity agencies, including CISA and the FBI, have issued advisories urging critical infrastructure entities to enhance their cybersecurity defenses. Recommendations include securing network devices, ensuring software is up to date, and adopting comprehensive security protocols. These steps are essential in mitigating the risk of infiltration and safeguarding against potential attacks.
Volt Typhoon has exploited zero-day vulnerabilities in widely used security systems, such as Fortinet’s FortiOS SSL VPN and Ivanti’s Connect Secure VPN, allowing unauthorized access and potentially leading to data breaches and system control.
This critical zero-day vulnerability highlights the significant risk that such exploits pose to the security and integrity of VPN infrastructures. CVE-2024-21762 (CVSS: 9.8) is an out-of-bounds zero-day vulnerability, while CVE-2024-23113 (CVSS: 9.8) is a vulnerability due to the use of an externally-controlled format string, and CVE-2023-27997 (CVSS: 9.8) is a buffer overflow. Exploiting these vulnerabilities allows attackers to bypass authentication or execute arbitrary code, posing a severe threat to organizations that rely on this VPN for secure remote access.
The group Volt Typhoon has exploited vulnerabilities in Ivanti Connect Secure systems. Specifically, they have taken advantage of CVE-2023-46805 (CVSS: 8.2), an authentication bypass vulnerability; CVE-2024-21887 (CVSS: 9.1), a critical command injection vulnerability; and CVE-2024-22024 (CVSS: 8.3), which allows an attacker to access internal files by sending maliciously crafted XML files. These vulnerabilities allow attackers to bypass security controls and execute malicious commands, posing a significant threat to network security and data integrity.
Source: CISA
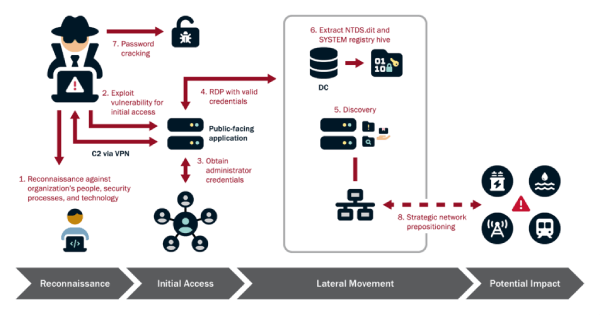
Volt Typhoon begins by carefully analyzing the target organization’s network and operational protocols. This helps them understand the network’s security measures, typical user behaviors, and identify key IT personnel. They use this intelligence to enhance their operational security, making sure their actions blend in with normal network activity. For example, they may use compromised credentials during regular working hours to avoid detection by security systems.
The group’s initial access to targeted organizations often exploits vulnerabilities in internet-facing devices, such as firewalls, VPN appliances and routers. By leveraging any privileges afforded by these devices, Volt Typhoon extracts credentials to Active Directory accounts used by the device, attempting to authenticate to other network devices with these credentials. Furthermore, Volt Typhoon enhances the stealth of their operations by proxying their network traffic through compromised Small Office/Home Office (SOHO) network edge devices from manufacturers like ASUS, Cisco, D-Link, NETGEAR, and Zyxel. This tactic not only obscures their activities but also reduces their infrastructure costs, demonstrating a sophisticated understanding of network vulnerabilities and operational efficiency.
Once Volt Typhoon gains access, they engage in hands-on-keyboard activity, leveraging command-line interfaces for exploration and execution of their objectives. Remarkably, Volt Typhoon’s post-compromise activity rarely involves malware; instead, they rely on living-off-the-land commands for information gathering, network discovery, and data exfiltration. This approach minimizes their digital footprint and complicates detection efforts.
A key goal for Volt Typhoon is obtaining administrator credentials, often by exploiting privilege escalation vulnerabilities or accessing credentials stored insecurely on network appliances. With valid administrator credentials, the group moves laterally within the network, targeting domain controllers and other critical devices. They employ tactics like dumping credentials from the Local Security Authority Subsystem Service (LSASS) and extracting information from web browser applications, showcasing their deep technical acumen and persistence.
Volt Typhoon’s command and control (C2) operations are characterized by the use of valid credentials for system access, similar to authorized users, which makes detection challenging. In some cases, they create proxies on compromised systems to facilitate access, employing built-in commands like netsh portproxy or utilizing custom versions of open-source tools for establishing a C2 channel. This level of sophistication in maintaining communication with compromised systems underscores the advanced nature of Volt Typhoon’s cyber espionage activities.
Earlier this year, the U.S. Justice Department disrupted a botnet (KV botnet) of hundreds of U.S. based small office/home office routers hijacked by Volt Typhoon. The vast majority of routers that comprised the KV Botnet were Cisco and NetGear routers that were vulnerable because they had reached “end of life” status; that is, they were no longer supported through their manufacturer’s security patches or other software updates. The court-authorized operation deleted the KV Botnet malware from the routers and took additional steps to sever their connection to the botnet, such as blocking communications with other devices used to control the botnet. While the demise of the Volt Typhoon KV Botnet by the FBI poses a victory over the threat group, U.S. agencies continue to be highly concerned about the threat that this group poses to organizations and critical infrastructure.
Addressing the threats posed by actors like Volt Typhoon requires a multifaceted approach to cybersecurity. Organizations must invest in behavioral monitoring to detect the subtle signs of Volt Typhoon’s activities and undertake comprehensive remediation efforts to secure compromised accounts. Closing or changing credentials for affected accounts and examining the activity of compromised accounts for any malicious actions are crucial steps in mitigating the impact of Volt Typhoon’s operations.
The Security Research Team in Versa Networks plays a crucial role in protecting its customers from emerging cybersecurity threats like Volt Typhoon. Their proactive approach in identifying, developing, and implementing detection rules is vital for maintaining strong security defenses.
Versa Networks has identified the issues and released SIDs (Signature IDentifiers) to mitigate vulnerabilities related to common Volt Typhoon attack tactics, in our latest offering of Security Package (SPACK) version 2127 and 2059.
| SID (Signature Identifier) | CVE |
|---|---|
| 1000017794, 1000017814 | CVE-2023-27997 |
| 1240110060 | CVE-2023-46805 |
| 1240110070, 1240110071 | CVE-2024-21887 |
| 1000019497 | CVE-2024-22024 |
These signatures are part of the Versa recommended vulnerability profile and customers will automatically get protection. Versa recommends that customers running a custom vulnerability profile select and activate the signatures to get protection. Customers can visit our Support Center to obtain more information on SPACKs 2127 and 2059.
In addition, Versa Networks customers benefit from enhanced protection provided through our Zero Trust Unified SASE (Secure Access Service Edge) platform. Enterprise-wide protections from vulnerabilities are provided by:
A cloud-delivered replacement for legacy VPN, Versa ZTNA delivers private connectivity for users who are working remotely, as well as Zero Trust access for users who are on-premises (on-site). With this solution, remote employees can securely connect to applications anywhere, anytime, from their device of choice, based on the principle of Zero Trust access. Versa ZTNA extends to the local on-premises environments, and Zero Trust access is similarly enforced for users in the branch, campus or data center, limiting lateral movement inside the network.
Cloud-managed and cloud-delivered, VSIA secures enterprise sites, home offices, and traveling users accessing distributed applications without compromising security or user experience. URL filtering with IP reputation inspects all incoming and outgoing traffic for malicious exploits and known malicious domains, including those associated with the vulnerabilities, and will block associated IOCs.
Provides comprehensive security coverage and can help to block attacks in real time arising from the vulnerabilities via security packs and sandboxing, together with other elements within the VSIA product offering.
scanning of email and inline Web, SaaS, private and Internet applications detects and prevents exfiltration of sensitive information via the network. Versa Network DLP monitors, detects and blocks illegal or unauthorized exfiltration of data while it is in motion across the network, using 25 discrete content types and multiple scanning methods.
IP Addresses associated with the IOC’s:
176[.]102[.]35[.]175
184[.]67[.]141[.]110
194[.]50[.]159[.]3
49[.]204[.]73[.]250
61[.]2[.]141[.]161
82[.]117[.]159[.]158
114[.]143[.]222[.]242
117[.]211[.]166[.]22
183[.]82[.]110[.]178
192[.]149[.]47[.]110
208[.]97[.]106[.]10
210[.]212[.]224[.]124
212[.]11[.]106[.]139
24[.]212[.]225[.]54
45[.]63[.]60[.]39
46[.]10[.]197[.]206
49[.]204[.]65[.]90
49[.]204[.]75[.]90
49[.]204[.]75[.]92
70[.]60[.]30[.]222
80[.]64[.]80[.]169
89[.]203[.]140[.]246
93[.]62[.]0[.]77
94[.]125[.]218[.]19
https://www.techtarget.com/searchsecurity/news/366569675/CISA-warns-Fortinet-zero-day-vulnerability-under-attack
https://www.microsoft.com/en-us/security/blog/2023/05/24/volt-typhoon-targets-us-critical-infrastructure-with-living-off-the-land-techniques/
https://www.tenable.com/blog/volt-typhoon-cybersecurity-advisory
https://www.tenable.com/blog/cve-2023-46805-cve-2024-21887-zero-day-vulnerabilities-exploited-in-ivanti-connect-secure-and
https://otx.alienvault.com/pulse/65a66bcaf64bd55d8740cc8d
https://www.cisa.gov/news-events/cybersecurity-advisories/aa24-038a
Subscribe to the Versa Blog