Best Practices for the Enterprise (Part 1)

Principal Architect
August 16, 2019
Welcome to my Enterprise Best Practices Blog. My name is Neil Danilowicz, and I am a Principal Architect for Versa Networks. Over the next few months, I will delve into best practices for Enterprises as they begin their journey into Software Defined Networking, especially Software Defined Wide Area Networking (SD-WAN).
Today, security is a boardroom topic and on the forefront of every large enterprise. From the recent security breaches at Yahoo, Target, and Equifax, there is broad awareness of how a slip in security can damage the brand and tarnish what took years to build. With digital transformation, embracing multi-cloud/SaaS and mobility creates additional threat vectors that an enterprise must consider in their security framework.
Let’s face the facts. The attack vectors are ever changing, and the hackers (threat actors) are becoming more sophisticated and better equipped. Therefore, the question is not “If the network is going to be breached or compromised?”, the question is “When will the enterprise be breached, and how well can the attack be contained to mitigate damage to the enterprise brand?”
Just like you protect your home with locks at the front door but also protect key valuables inside the home with safes — in an enterprise, security is needed not just for the protection of the perimeter; it’s also needed for internal data, intellectual property and customer data.
Enterprises in certain verticals need to satisfy many regulations such as PCI, HIPPA, SOX, or other Federal regulations, which often requires proof that the enterprise is impervious to various attacks (DDoS, malware, viruses, or industrial espionage).
The transition to multi-cloud/SaaS and mobility is enabling business agility. As enterprises embrace these transitions, they must transform their wide area network with SD-WAN, and security needs to be at the forefront. Enterprises should consider the following the building blocks for deploying a Secure Network:
- Certificate based access control
- Threat management platform
- Encrypted communications
- Key management
- Key negotiation
- Encryption algorithms
- Key lengths
- Certificates
- Multiple firewall capabilities
- Define a secure network perimeter
- Log access attempts
- Multi-tenancy
- Micro-segmentation
- Threat detection
- Threat prevention
- Segregated Control and Data Planes
- Multi-tiered Role Based Access Control (RBAC)
- Multi-tiered Control Plane
- Full Visibility
- Extensive logs
- Flow data
- Action records
- Violation notifications
- Black listing
- Predictive Analysis
While most of these items individually provide a layer of protection, a multi-layer approach is needed for an effective architecture that is scalable and safe while also being simple to deploy and manage.
For ultimate protection, secure networks utilize a multi-tiered architecture where multiple checks, authentications and authorizations are required to gain access to the internal network. Typically, in this design, critical data is not stored or accessible directly from the demilitarized zone (DMZ).
Cloud-based services and SaaS providers are all the rage these days, but to provide optimal user experience, enterprises must distribute their security perimeter and provide direct Internet access (DIA) at multiple sites for a faster on-ramp to these cloud services. Additionally, using Internet for site-to-site connectivity (instead of or in addition to private circuits like MPLS or PIP) puts an Internet connection at every site in the network. In this distributed environment, an enterprise must now protect the company network from an increased threat surface. While most vendors will offer a bolt-on security framework, it does not fully address the needs and an enterprise needs to be aware of the Secure Tiered Architecture.
Buyer Beware
On the surface, all SD-WAN solutions show a promise of cost reduction and application awareness relying on some mechanism of building secure tunnels between sites. However, you need to look deeper at how this overlay is built – including the approach used to do key exchange and where the keys are stored.
Some SD-WAN solutions require that every branch connect over the underlay transport (including Internet) to a central manager which has a repository of sensitive information about various branches and the Enterprise. Databases containing sensitive information should never directly be exposed to Internet, even if the connection to the database-server is made over an encrypted connection. Why? Time and again, we have seen that the bad guys (threat actors) can exploit certain vulnerabilities in the system, especially if the system is directly exposed to the Internet.
A solution where every node has direct access to the “Keys to the Kingdom” implies that others can gain access to those same “Keys.” While some may argue that current algorithms are yet to be broken, we know well that where there is a will, there is a way. And the key word here is YET.

When 128-bit keys were introduced, many felt that these were secure and would probably be secure for years to come. But Moore’s Law proves that as technology advances so do the weaknesses in prior security postures.
• Does the solution support an enterprise specific Certificate Authority (CA)?
• Can the solution provide the ability to have multiple CA’s that give flexibility to move with speed and
agility?
• Can the vendor provide Vulnerability Assessment Testing and Penetration Testing results for all their solution components?
Why Choose Versa?
Versa Networks offers a multi-tiered architecture for Enterprises considering SD-WAN that is mature, hardened and validated by independent entities as well as enterprises and service providers.In Versa’s implementation, the configuration and the “keys to the kingdom” are not directly accessible from any zone. These keys are pair-wise, can be rotated constantly and never sent as a full key on any wire. Additionally, all information is proxied via a secure connection by an IPSec tunnel through a Secure Gateway.
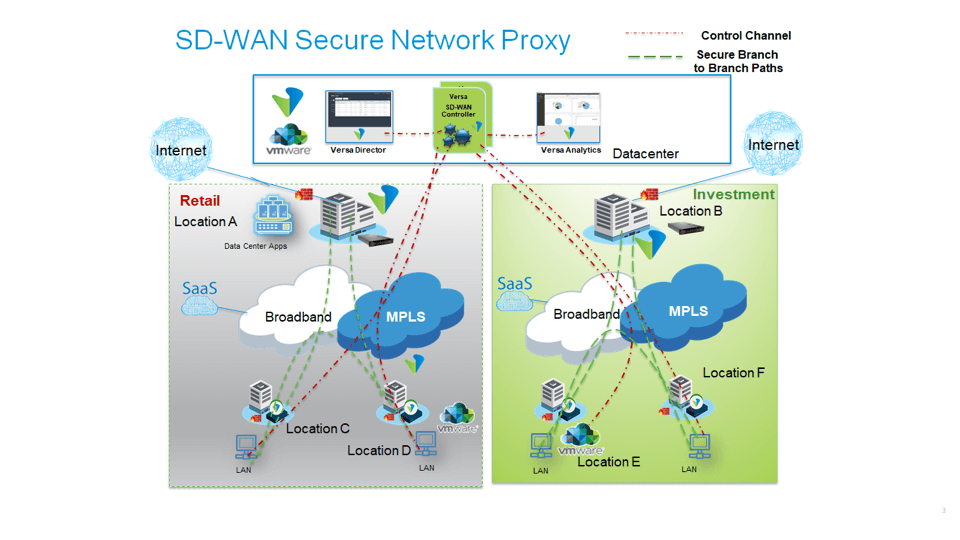
Versa’s solution incorporates SD-WAN as well as Stateful Firewalls, NextGen Firewalls, or UTM Firewalls. Versa’s NextGen Firewalls are NSS recommended for the Second Year in a row having achieved a 99% efficiency in Exploit Block Rate. Versa’s SD-WAN has Intrusion Detection System (IDS), Intrusion Prevention System (IPS) and Anti-Virus detection mechanisms built into Versa VOS™ (formerly FlexVNF) to assure that even approved connections do not contain Trojan Horses or other issues. Also, Versa utilizes application heuristics to assure that connections that purport to be a given application are behaving, in actuality, like that application. For example, a Secure Copy Protocol (SCP) transfer should not look to inject SQL instructions to the end host.

These capabilities can be applied at the edge or at aggregation points or even at the exit points of the network, or they can be applied at all levels to provide multiple layers of protection.
Versa’s SD-WAN solution even provides for third-party integration for network services functions. If the Enterprise wants to use a third-party Firewall, or IPS or IDS or A/V Solution, then this is currently supported in the service chaining capabilities within Versa SD-WAN. These third-party service functions can either be appliance based or virtual functions (VNFs). In fact, the virtual functions can even be instantiated on Versa VOS™ (formerly FlexVNF) uCPE.
So, in conclusion, as Enterprises begin their journey into SD-WAN, they should look to implement SD-WAN solutions that have a strong security foundation – Multi-layered, Multi-tiered, and with many bells and whistles.
Until next week, when we will focus on Key Exchange and why that is important for securing the Network.






