Apache: Failed to Harden in 2017

Versa Networks
October 10, 2017
Apache’s gaps has been in news for quite a while, and this has led to the massive milestone of Equifax being compromised to the tune of 143 million records. This has been a difficult year for Apache, with so many vulnerabilities being reported. Refer to the link for a list of Apache vulnerabilities reported in 2017. Though previous years also accounted for large chunks of Apache vulnerability, this year it has been in news for two particular vulnerabilities, CVE-2017-5638 (which led to the compromise of user data through the Equifax breach) and CVE-2017-9805 (due to the fact that the public PoC was readily available).
About CVE-2017-5638 (Equifax data breach via Jakarta in Apache)
The Jakarta-based plugin in Apache, which is used to process the upload request, was victim to the said vulnerability CVE-2017-5638, and eventually this was also the cause of the data breach in Equifax, which lead to leak of tens of millions of user data records. In order to exploit this vulnerability, the attacker needed to send a crafted request to upload a file to a vulnerable server running Apache Struts version 2.3.5 – 2.3.31 and 2.5 – 2.5.10 with Jakarta plugin installed. A PoC to demonstrate the attack scenario is publicly available.
On dissecting the information available by taking a diff of the patch, it was found that the usage of class LocalizedTextUtil was removed, which was meant to reflect the error to the user if the upload using a multi-part HTTP request fails.
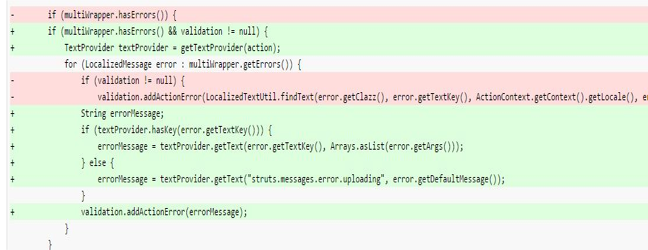
To display an appropriate error message, function findText() is used which references the appropriate error message from the table below (Error Messages). This function processes the locally saved messages against the given error key. If the message is found, it is treated as OGNL expression and evaluated. If the attacker is able to pass the crafted OGNL expression with multipart/form-data, it will be evaluated and hence able to execute arbitrary command remotely.
| Error Key |
Description |
| struts.messages.error.uploading |
A general error that occurs when the file could not be uploaded |
| struts.messages.error.file.too.large |
Occurs when the uploaded file is too large as specified by maximumSize. |
| struts.messages.error.content.type.not.allowed |
Occurs when the uploaded file does not match the expected content types specified |
| struts.messages.error.file.extension.not.allowed |
Occurs when uploaded file has disallowed extension |
| struts.messages.upload.error.SizeLimitExceededException |
Occurs when the upload request (as a whole) exceed configured struts.multipart.maxSize |
| struts.messages.upload.error.<Exception class SimpleName> |
Occurs when any other exception took place during file upload process |
(b) Error Messages
Versa Security Solutions
Versa has released the following rules to address this vulnerability. However, more rules may be added or the current rules may change depending on the additional vulnerabilities information available.
| Versa Signature ID |
Rule Name |
| 1170306030 |
Apache Struts Jakarta Multipart Parser Remote Code Execution |
| 1000011363 |
Apache Struts Jakarta Multipart Parser Remote Code Execution |
It should be noted that vulnerability was disclosed by Apache on 7th March 2017 and Versa’s signature was released on 15th March 2017 to address the issue. Later the signature was updated to address additional vulnerability information in October.




